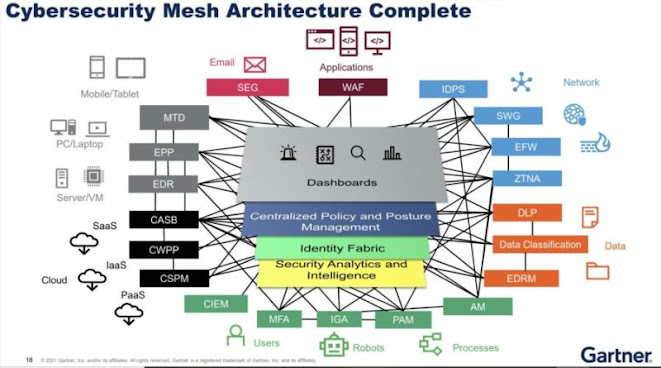
The second of Gartner’s “Top 8 Cybersecurity Predictions for 2021-2022” relates to one of their highlighted “Top Strategic Technology Trends of 2022” — cybersecurity mesh, also known as cybersecurity mesh architecture (CSMA).
“By 2024, organizations adopting a cybersecurity mesh architecture will reduce the financial impact of security incidents by an average of 90%.
While all organizations today encounter some degree of decentralized technology and access, cybersecurity mesh architecture will be particularly important to businesses that fully embrace remote working, work with a large number of third-party contractors, or have a widely distributed workforce. Basically, any organization where the majority of work doesn’t take place in a centralized, highly controlled location.
Even organizations that do return to a mostly office-based work environment should consider adopting CSMA as there’s virtually no way to prevent employees from working remotely on occasion or accessing data or applications (like email) from their personal devices or a company-owned mobile device on an uncontrolled network.
What Businesses Need to Know
Cybersecurity mesh builds on another popular cybersecurity trend, Zero Trust. Zero Trust introduced the concept of “don’t trust, always verify,” marking a departure from the assumption that once a user or device has been verified it remains verified. With Zero Trust Network Access (ZTNA), verification happens at every step — including around data, devices, applications and users.
Cybersecurity mesh takes that approach and extends it further to cover all users, devices, networks, etc. regardless of location. This is particularly important as more employees work outside of traditional office networks either full time or occasionally.
The concept of a traditional, controlled security perimeter no longer functionally exists for the vast majority of businesses. Any organization that continues to cling to this old cybersecurity approach will find themselves facing major issues.
What Businesses Need to Do
Cybersecurity mesh is a fairly new term and there aren’t many solutions that specifically address it on the market yet. [1] Businesses interested in working toward CSMA, however, should implement or mature their Zero Trust posture. There are many cases where ZTNA extends to outside use cases, bridging into the concept of cybersecurity mesh.
Within the next two years, organizations should adopt the concept of cybersecurity mesh by working to implement comprehensive solutions that specifically address verification and remote working situations. Implementing Zero Trust is a good start, but additional solutions are likely to emerge within the next 24 months as well.
To learn more about all the options available to you for meeting your organization’s data protection and network security requirements (including security posture and risk assessments, and awareness training and employee education programs) .... plus comparisons of 100s of best-in-class network security / cybersecurity providers and what they have to offer ... simply ask us at Network Security. It's as easy as 1, 2, 3. Labels: CIO, CISO, CSMA, Cybersecurity, Cybersecurity Mesh, Cybersecurity Mesh Architecture, Zero Trust, Zero Trust Network Access, ZTNA